GT-AMPTo Autenticação Multi-fator Para Todos
This project aims to develop a solution that allows the Brazilian Academic Federation (CAFe) to operate with multiple authentication factors on Shibboleth Identity Providers and translate the federated authentication to physical devices in the Internet of Things (IoT). This project started in 2017 and was completed in 2019.

There are five options of second authentication factor in our proposal:
- Phone prompt – first, the user inputs login and password in the IdP (first authentication factor), then the user receives a notification on his/her smartphone (GT-AMPTo App) to confirm that the user is truly trying to authenticate in his/her IdP.
- One-Time Password (OTP) – The Time-based One-Time Password (TOTP) [RFC 6238] standard is used by several 2FA solutions and smartphones has helped its rise. Smartphone TOTP applications have the advantages the possibility to use a unique application to manage all user TOTP tokens for different institutions.
- FIDO2 (WebAuthN) – FIDO2 is an industry standard for robust authentication and in this work we choose it to offer an 2FA option that does not depend of smartphone or even a 2FA device that relies over an Internet connection. Currently, our solution supports only one associate FIDO2 USB key per user account.
- Biometric Authentication (FIDO UAF) – after the first authentication step, the user proves his/her identity using a biometric authentication app (GT-AMPTo App) in the smartphone. In this authentication process, no biometric data is shared, only the authentication confirmation is provided to the IdP.
- Backup codes – In our solution when the user associates a second factor to his/her account, a set with ten disposable codes are generated automatically and the user is invited to print or save them in a file. Each disposable code can be used only once.
Solutions that rely on Phone prompt, also called push dialog, aim to increase the robustness of the authentication process with a minor impact on the usability. This 2FA technology requires a smartphone and its operation is quite similar to the TOTP scenario. The user receives a notification on his/her smartphone, which opens a prompt with a simple question: Are you trying to authenticate right now? (Yes or No). It is more user friendly compared to the TOTP solution.
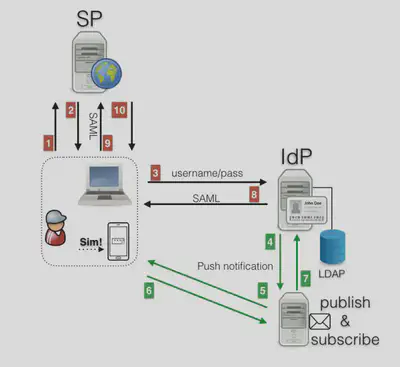
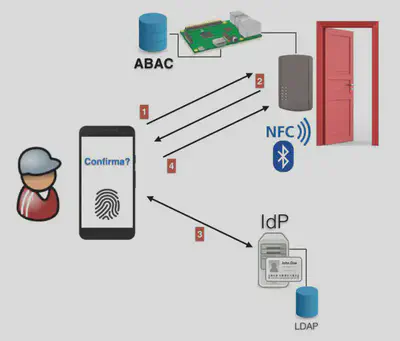
In the IoT scenario, the biometric authentication (FIDO UAF) in the user device is the only authentication factor considered. In this scenario, the user makes use of federated authentication to physically access an environment in an institution that he/she is visiting.
Source code
The source code and the install instructions are available at https://git.rnp.br/GT-AMPTo/mfap-installation-guide. The source code is under Apache License Version 2.